Apart from developing pieces of tech, I also like to “break” pieces of tech. By “break”-ing, I mean I like to discover how a piece of tech can be creatively abused for a purpose that it is never been intended to be normally used. Officially some people call it “bug hunting”.
About
This post is a write up of how I found a valid:
A simple bug, yet a P1 priority in Google’s Gsuite product, that took about 20 minutes to discover & create POC.
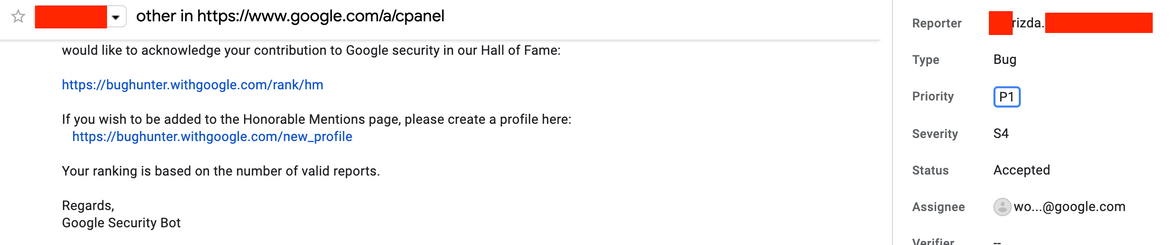
It also get me into Google’s Bughunter Hall of Fame - Honorable Mention.
The bug is very simple that I don’t need any backend/terminal based script to make the exploit scalable, I just used Web Browser (and its HTML+JS capability) for the entire discovery and Proof of Concept development process.
Bug Summary
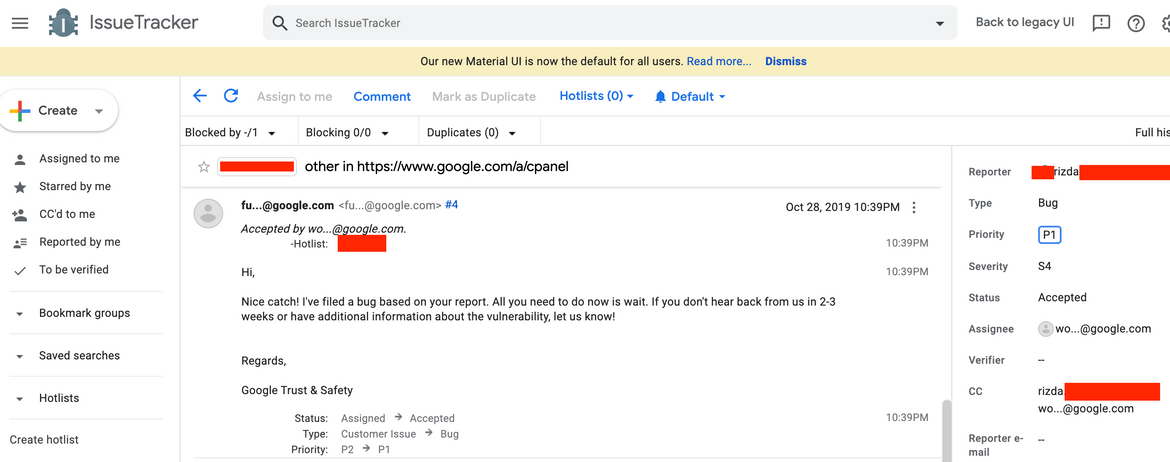
GSuite is leaking info about if a company (or a domain) is using GSuite, that may escalate into privacy issue, via image company’s profile-logo’s url.
Details
Steps to reproduce:
-
Simply visit this URL
https://www.google.com/a/cpanel/REPLACEME.COM/images/logo.gif?service=gmailNote: replace the REPLACEME.COM, with real target web domain
- You will be able to see the company custom logo if they are using GSuite, (else you will see default outdated google app logo as indication target are not using GSuite).
- That’s it. POC can be seen on POC section below.
Practical examples:
- Atlassian is one of listed Gsuite customers. So their Gsuite logo URL will be: https://www.google.com/a/cpanel/atlassian.com/images/logo.gif?service=gmail . Visit the URL and you will see Atlassian logo.
- Wikipedia.com is not Gsuite customer. So when you visit https://www.google.com/a/cpanel/wikipedia.com/images/logo.gif?service=gmail you will see default Google app logo instead.
Possible Attack scenario:
- Anyone can easily test list of domains to check if those domains are Google GSuite customers.
- Additionally Simply using JS+HTML (link below) we can reliably scan entire Fortune 500 company’s domain to see if they are using GSuite within just seconds.
Proof of Concept:
JS Fiddle Demo: https://jsfiddle.net/0d5qfkm9/
Timeline
- Oct 24, 2019: Reported
- Oct 24, 2019: Triaged
- Oct 28, 2019: Accepted, assigned as P1 priority
- Nov 15, 2019: Escalated, eligible for Hall of Fame - Honorable Mention
- Jan 25, 2020: 90 Days deadline expired, allowed to make public disclosure
- Mar 28, 2020: This blog created for public disclosure, Bug status still open (accepted) without fixDiscovery Process
The Company I work for use Gsuite for its email service. Then I realized that there is Company logo displayed on the web page of the email service.
 *not my company’s logo, just fake illustration
*not my company’s logo, just fake illustration
Feeling adventurous, I quickly pulled inspect-element feature from Chrome Dev Console Tools, to see the image’s URL. Then I realized:
- It is an easily guessable/enumerable URL, based on the Company’s domain name (Gsuite customer’s domain name). e.g:
https://www.google.com/a/cpanel/atlassian.com/images/logo.gif?service=gmail - If the domain is not Gsuite customer, it will just shows generic Google app logo.
I thought I can quickly create a backend/terminal based script to check a list of domains, and see if their logo shows up. But it will be a bit complex to determine if the company logo shows up or Google app logo shows up. I checked that most of company logo have different image size from the default Google app logo, so I leverage the image size.
As a web platform enthusiast, I know HTML/JS must have some API to get the image size, and quickly developed a logic to differentiate between non-default (customer’s logo) image size vs default image size. And yes, there you have it, HTML+JS is enough to create a powerful POC.
Closing
I’ve done security bug hunting as hobby in my free time, not in a professional level, because probably I prefer “making” stuff more than “breaking” stuff. For fun, I have some experiences performing RCE (VM root account take over), lots of source-code infiltrations, database infiltrations, XSS, etc. to local Startups, Government, and occasionally Big Tech Company like this. But I haven’t got time to make write up about those (I did report some of it, but haven’t got time to report for the rest). But this one bug is simple yet fun, so I made one.
This might be not a good write up by any standard, but hopefully will make me learn to write some better ones in the future. See you on the next one!
Fun fact:
It took me longer to write this write up, than the entire discovery process :)